In settings as diverse as data centers, healthcare facilities, and remote telecom equipment sites, the demand for stricter physical security that can be managed with a full audit trail is growing. For these applications, managers are seeking solutions for simplified access control and credential management, outside of traditional lock-and-key solutions.
In many cases, the cost and complexity of networked security installation and IT support become considerable road blocks to implementation. While electronic locking solutions are the ideal choice for site-specific security, the increased wiring, installation, and IT support costs when integrating these solutions into existing networks have led to a search for more efficient solutions.
There are scalable solutions available that provide complete, remote access control without a wired network connection or software to buy, install, and manage. Specifically, wireless solutions based on Bluetooth communications provide a more straightforward approach—one that is fully secure—and provide a solution that provides an audit trail and can be cost-effectively implemented to secure a wide range of equipment and locations.
Perceived Complexities for Electronic Locking Solutions
The use of electronic locking solutions in a wide range of locations and operations has been widely accepted for some time. However, there has developed a perception that the implementation of fully connected electronic locking solutions requires significant hardware and IT investment and ongoing support, which in certain applications can lead to inadequate solutions or a reliance on traditional, mechanical lock-and-key access management.
In data centers, for example, a common way of implementing rack-level electronic control assumes investment in multiple systems. An electronic lock is installed on the rack; that lock would connect to some sort of controller inside the rack. Then that rack would have to be tied back through a switch, which would connect that controller into a network. At a large data center, multiple switches would need to be provisioned and integrated into a backbone—one that is separate and parallel to the backbone connecting the servers in the racks.
Software would have to be implemented and managed on this “electronic lock network” to manage all the different assets, as well as the audit trail and assignment of electronic keys via either RFID cards or smartphones with Bluetooth access, to unlock a given rack.
All the physical and virtual networking for this type of solution would necessarily involve IT departments, adding further complexity to what is essentially a security function: electronic access control.
Wireless Access Control and Audit Trail Reporting
Wireless solutions based on Bluetooth communications offer a simplified solution for physically securing equipment such as data center cabinets and mobile nursing stations. The controller is simply wired to a power source and to the electronic lock without the need for other discreet components, allowing for remote access without the need for costly, complex network connections.
There are two options for providing access to equipment with Bluetooth lock controllers: by using a smartphone directly, or with existing RFID access credentials.
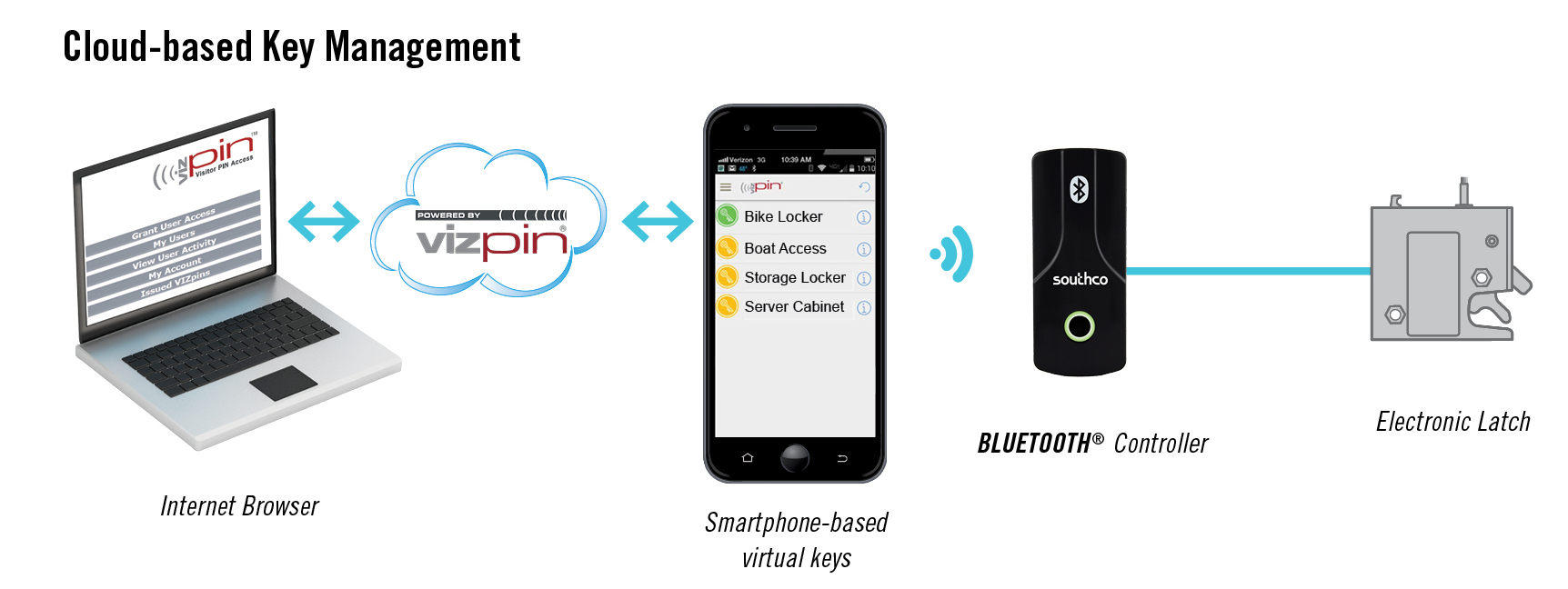
Southco’s BT Bluetooth Lock Controller provides remote access control and monitoring of intelligent locks without having to physically connect to a network, or install, manage and maintain software.
Smartphone Access
A Bluetooth-enabled smartphone is one convenient device for functioning as a “key” to access equipment with electronic locking mechanisms. Individuals who are to be authorized for accessing equipment—technicians in a data center, for example—will have an app on their smartphones. Time-based virtual keys can be sent wirelessly to the app via a cloud-based web portal.
To access the secured equipment, the technician approaches the rack and touches the access button on their installed app, which transmits the encrypted Bluetooth signal to the lock controller, unlocking the door and sending a record of the access via the smartphone app to the cloud.
Each lock controller has a unique, algorithm-based identity, which is stored in the remote web portal database. When the smartphone app sends its Bluetooth signal, it contains that specific controller’s digital identity, enabling the lock release.
The Bluetooth device does not require a wireless network to open the lock. The smartphone simply communicates via Bluetooth with the lock controller. The lock controller is wired only to the lock, not to any other network. Each time access occurs, a digital audit trail is generated and sent using a wireless network connection to the remote web portal, via the cloud.
This is a highly secure approach: The electronic key loaded to the app will typically have a limited timeframe during which it can be used. If it expires, the technician must re-access the cloud for re-authorization. In addition, the Bluetooth signal has 128-bit encryption, protecting it from hacking; furthermore, because the lock controller is not tied to a network, it’s not a point of vulnerability for hackers.
RFID Access
As an alternative to Bluetooth access from smartphone apps, electronic lock controllers may also accept input from traditional RFID readers. Users can access the equipment using traditional RFID cards, following the same basic protocol; the lock controller is a Bluetooth-enabled device that periodically uploads and downloads credential information, along with audit trail data sent to a wireless tablet or other device.
The audit trail is pushed from the Bluetooth controller to a wireless device and up to the cloud, where it can then be accessed by the data center’s central office. Administrators can assign and revoke RFID cards using the same cloud-based web portal.
This is a convenient approach for settings where smartphones are not permitted to be used; these can include factory floors (where there is proprietary equipment or a work rule restricting smartphone usage) or hospital/healthcare settings (where HIPPA regulations set strict requirements concerning patient records). Personnel in these locations can unlock or access equipment using their personal RFID cards.
RFID and smartphone access can also be used together to access the same piece of equipment. In situations where not everyone has a smartphone, users can access the equipment with either an RFID credential or Bluetooth-enabled smartphone. To obtain the audit trail when using RFID credentials, a Bluetooth wireless device connected to WiFi would be used as the vehicle for exchanging access control data between the controller and cloud.
The remote monitoring and enrollment of credentials can be managed via the web portal, with any changes being pushed back to the smartphone through the cloud. The smartphone then transmits this data wirelessly to the lock controller.
Scalable Access Control
Bluetooth wireless, cloud-based solutions offer a simplified, scalable means of adding additional access points with minimal installation and setup. The flexibility provided by Bluetooth controllers allows the data center manager to grant access to personnel from anywhere without having to physically be on site at the data center when access to equipment is necessary.
Once virtual keys have been delivered to a smartphone or added to existing credentials, WiFi access isn’t required for communication between the Bluetooth-enabled phone or RFID card, and lock controller.
The scalability offered by this approach isn’t limited to a single data center or other location—it can ultimately leverage the power, ubiquity, and scalability of cloud-based computing. Cloud computing has been gaining rapid acceptance for a wide range of enterprise applications, and cloud service providers make continual and major investments to ensure that their platforms are the most secure and safe systems available.
By outsourcing the web portal, audit trail, and permissions management of the wireless lock access to the cloud, long-term savings can be realized because IT departments will not need to set up and manage these security applications as part of their enterprise computing platform. Also, cloud-based management makes it easier to manage secure access to multiple locations from a central office.
Multiple Application Benefit from Wireless Access Control
Electronic locks with integrated audit trail can be used to secure and manage access to a wide range of equipment and locations; along with data center racks, these include:
- Automated teller machines: Security companies servicing and refilling this equipment need simple, time-based access to this equipment, with secure audit trails.
- Remote telecommunications equipment: Many telecom networks have remote, stand-alone equipment, such as cellular sites and local switching systems; these need periodic access by technicians for repair and configuration work. Rather than running parallel access systems, use of Bluetooth access controllers is a simpler solution that still satisfies security requirements.
- Healthcare charting stations: A common sight in hospitals and rehab centers is mobile nursing stations equipped with computers and touchscreens that nurses and other professionals move from room to room. These stations need to be secured to protect patient privacy, and many healthcare organizations now seek audit trails of who accessed and used a given charting station; Bluetooth- or RFID-enabled electronic locking systems provide an efficient solution.
Conclusion
Bluetooth access controllers that have been integrated with intelligent electronic locks provide significant benefits for physical security management, providing simplified credential management and audit trail monitoring without having to wire into a network. By adding Bluetooth-controlled electronic locks to sensitive equipment, managers can control access, protect valuable data, and ensure compliance with appropriate regulations.
Filed Under: M2M (machine to machine), FASTENING • JOINING • locks • latches • pins