Last week, eSentire Threat Intelligence observed an increase in targeted attempts at exploiting small-office/home-office (SOHO) and consumer-grade network devices manufactured by global network solutions provider Dasan, and networking equipment from D-Link. The activity was identified using automated analysis via a simple script written in the form of a complex equation as seen below.
B = (sum(x[i] * y[i] for i in xrange(N)) – 1./N*sum(x)*sum(y)) / (sum(x[i]**2 for i in xrange(N)) – 1./N*sum(x)**2) A = 1.*sum(y)/N – B * 1.*sum(x)/N
Fortunately, these attacks appear to have steadily dropped since the last major documented spike on June 1, when a surge of exploitation attempts from more than 3,000 source IPs implemented an array of attacks against D-Link 2750B and Dasan GPON routers. None of the exploitation attempts observed against eSentire customers were successful, and it is unknown whether this attack had any effects on home networks, where these devices are more likely to be deployed. What’s even more unsettling is how successful recruitment can potentially arm any associated threat actor(s) with DDoS artillery, enabling these individuals to facilitate espionage of private browsing habits.
Botnets built from compromised routers may eventually be offered as another service to other threat actors, who can utilize these networks to further extort DDoS victims (among other users).
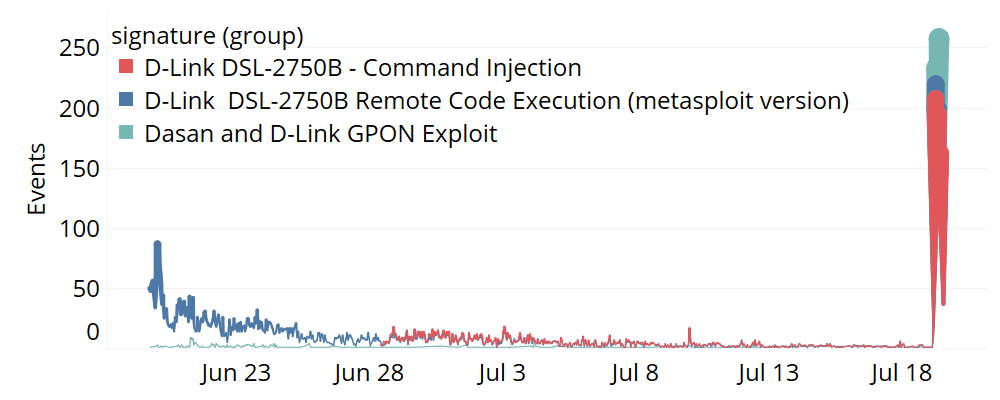
Figure 1: Router exploits in the last two months. (Image Credit: eSentire)
The botnet’s coordination indicates a single entity controlled the source IPs that tripper router exploit signatures over a 10-hour span, as Figure 2 shows.
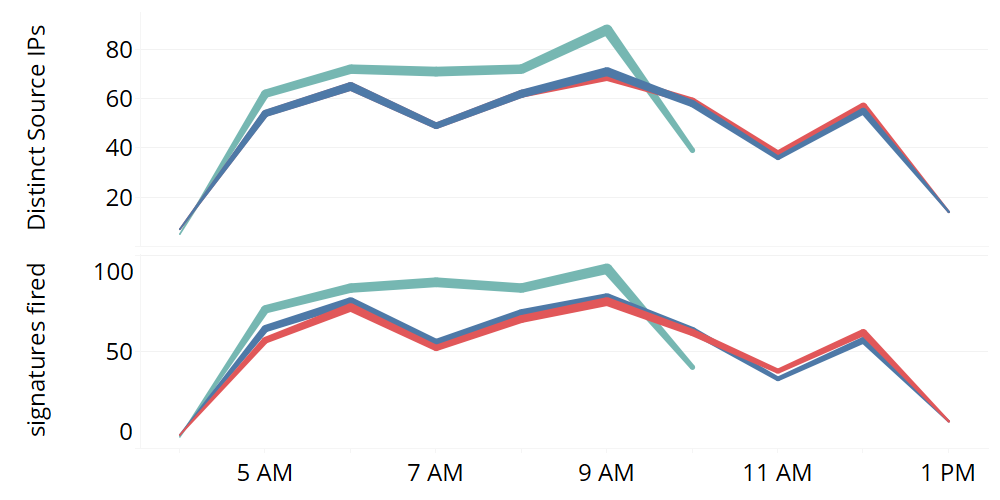
Figure 2: Number of distinct source IPs (top) and signatures fired (bottom) over the 10 hour campaign. See Figure 1 for color legend. (Image Credit: eSentire)
Exploits against Dasan GPON routers (CVE-2018-10562) that were recently announced appeared to have shorter life spans than the two other signatures, ending at 10 a.m. To further explain the coordination of the distributed attack against every affected organization, consider how the number of IPs attempting router exploits against each company was roughly equivalent to how many times the client experienced a particular signature being triggered (shown in Figure 3).
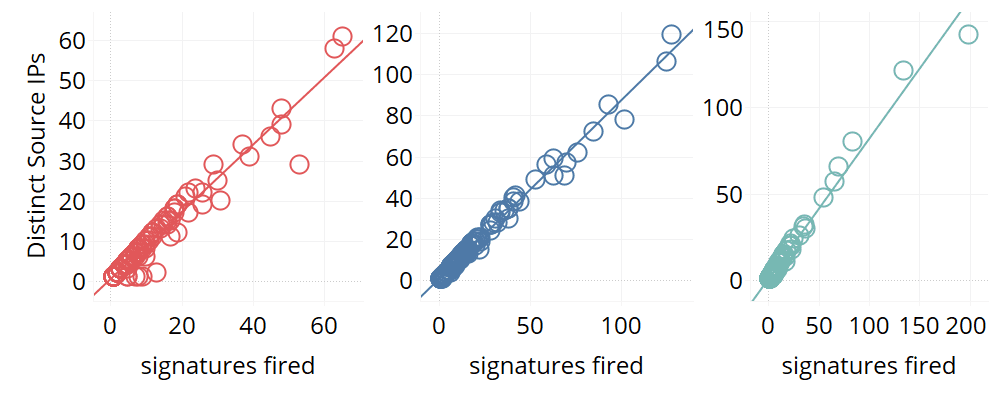
Figure 3: For each signature type (color) for each client (individual circles) the number of distinct IPs is compared with the number of signatures fired. Several outliers were removed. (Image Credit: eSentire)
The observation supports the proposition that the source IPs involved in the cyberattack were coordinated by a single-source command, so overall, this feature could be used to help automatically detect similar coordinated attacks in the future.
Taking IPs as shorthand for distinct source IPs, deviations contained in the linear trend existed for IP > 60 (for the command injection that Figure 3 shows), IP > 120 for the remote code execution attempt, and IP > 150 for the GPON exploit. The result of larger-sized organizations having a larger exposed threat surface can be likely attributed to higher variability. This makes an attacking IP more likely to make contact with multiple organizational assets, thus increasing the number of signatures raised.
Filed Under: M2M (machine to machine)